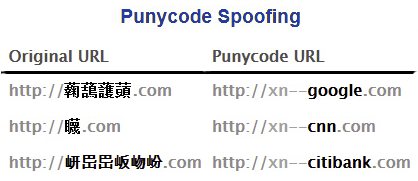
Punycode is an encoding system that serves to represent a sequence of unicode characters via an ASCII character sequence, to make it possible to use these sequences in domain names, without having to modify existing infrastructure and standards.
In this way you can manage internationalized domain names (IDNA) by adding the characters ‘xn–‘ to the beginning of the punycode string.
For example, by entering xn–google.com as address, we will see the browser show the string converted into Chinese characters:
The translation of Punycode sequences into the original encoding is the responsibility of the user agent (application installed on the user’s computer that connects to the server) in the browser.
The problem is that like all registered internet domain names, it is possible to create ad-hoc punycode sequences to show the user a completely converted string at will.
For example, if we insert the punycode string “xn–80ak6aa92e.com” into the browser (proceed only at your own risk), we will instantly see it converted to “apple.com”.
Obviously the open site will not be the official Apple site, but in reality it will always be the site “xn–80ak6aa92e.com”, only that our browser will display the transcoded text in ASCII.
In short the browser is misled, and with it the user, let’s see the example:
if we insert:
![]()
and press send, we will get the reply:
![]()
note the presence of an SSL certificate (DV) on the fake site, which creates a FALSE sense of security
THE DIFFERENCE BETWEEN THIS AND THE REAL ONE
![]()
in this case the SSL certificate (OV or EV) certifies the actual correspondence of the company.
The phenomenon of ‘phishing’ (a type of scam carried out on the Internet, especially by e-mail) is always looking for new strategies to mislead users, pushing them to click on links that ALWAYS SEEM trustworthy but that in reality a RE-INDIRECT to often harmful web pages.
These are social-engineering attacks in which an attacker tries to deceive the victim by convincing them to provide personal information, financial data or access codes, pretending to be a reliable entity in digital communication.
FIRST RULE: PREVENTION
When you receive emails of dubious origin, be wary of clicking on proposed links, especially if they are related in some way to banking or credit institutions.
Pay special attention to the address of origin, and before clicking on a link, check its actual destination.
Example:
a link displayed as “apple.com”, could actually be intended for the previous “xn–80ak6aa92e.com” (this could result from an HTML formatting built especially for the occasion)
In this case, however, simply place your mouse over the link and check the real link by reading the popup that appears (usually) at the bottom left of the mail program
SECOND RULE: CONTROL
Once you click on a link, how do you know that the site you are opening is actually the safe one?
The only defense you have in this case is the SSL certificate, which can be one of 3 types:
– DV Domain Validation: they guarantee an encrypted connection with the server, but they do not guarantee the company correspondence to the display name.
– OV Organization Validation & EV Extended Validation: in addition to encryption with the server, they guarantee verification of the effectiveness of the company.
If you look at the previous images, you can see the difference.