Everything you need to know about
Connections – Protocols – Modems – P2P – Browser – HTML – WWW – Viruses – Antivirus – Firewall – Ports – Your IP – Speed Test – General Facts
WHAT IS A CONNECTION
The network connection
 In general, a computer is said to be connected to the Internet and therefore host of the network once, after authentication with the connectivity service provider, it has obtained the IP configuration manually and statically by a network administrator or by dynamic assignment with DHCP, ready to start its web browsing session or to use other services offered by the network. This connection is typically obtained via modem, ADSL, wireless connections or internet keys. Often the computers before being connected to the Internet are connected to each other in a local area network (LAN) and this is then connected to the Internet via a router or gateway.
In general, a computer is said to be connected to the Internet and therefore host of the network once, after authentication with the connectivity service provider, it has obtained the IP configuration manually and statically by a network administrator or by dynamic assignment with DHCP, ready to start its web browsing session or to use other services offered by the network. This connection is typically obtained via modem, ADSL, wireless connections or internet keys. Often the computers before being connected to the Internet are connected to each other in a local area network (LAN) and this is then connected to the Internet via a router or gateway.
Connection with 4G/LTE internet keys
 It is the wireless connection similar to cellular mobile radio networks, i.e. between mobile terminals scattered over a territory and base stations or in the radio interface of the cellular system to use telephony services and/or Internet access. In this case there are various possible types of connection: TACS, GSM, GPRS, EDGE, UMTS, HSPA, LTE. In each of these typically varies the policy of multiple access to the radio medium shared between several users and the typical modulation scheme.
It is the wireless connection similar to cellular mobile radio networks, i.e. between mobile terminals scattered over a territory and base stations or in the radio interface of the cellular system to use telephony services and/or Internet access. In this case there are various possible types of connection: TACS, GSM, GPRS, EDGE, UMTS, HSPA, LTE. In each of these typically varies the policy of multiple access to the radio medium shared between several users and the typical modulation scheme.
Modems, Routers and Switches
 MODEM allows the MOdulation and DEModulation of signals containing information; the device takes the name MODEM from the name of these two main functions. In other words, bit sequences are recoded as electrical signals.
MODEM allows the MOdulation and DEModulation of signals containing information; the device takes the name MODEM from the name of these two main functions. In other words, bit sequences are recoded as electrical signals.
The router (from the English routers) is, on a logical level, an internal network node responsible for level 3 switching of the OSI model. In other words, on a physical level, it is a network device that routes information packets by working on level 3 (network) of the OSI model, i.e. as routing between two or more neighbouring sub-networks thanks to their respective interfaces, each with its own address, or to other non-neighbouring sub-networks via routing tables on the transport network. Many routers intended for the domestic market incorporate access point functionality for Wi-Fi wireless networks and modems for connection to the Internet. In this case, it should be noted that the speed of connection to the Internet is not higher than that contractually agreed with the ISP provider (acting as a modem) while the speed of the Wi-Fi radio interface, which ranges from 54Mbit/sec and up depending on the release of the implemented protocol, this can only be used for internal connection to the local wireless network with the other connected terminals (acting as a Wi-Fi router).
In reality, if these devices were routed at local network level, with the exception of the modem, they would not be strictly speaking routers but switches.
 A switch (English ‘swɪʧ; in Italian it is called a switcher) is a network device or internal network node that deals with level 2 switching, i.e. Data-Link Level of the ISO-OSI model, i.e. addressing and routing within local networks through MAC addresses, selectively forwarding the frames received towards an output port, i.e. towards a precise recipient thanks to a unique address-port correspondence.
A switch (English ‘swɪʧ; in Italian it is called a switcher) is a network device or internal network node that deals with level 2 switching, i.e. Data-Link Level of the ISO-OSI model, i.e. addressing and routing within local networks through MAC addresses, selectively forwarding the frames received towards an output port, i.e. towards a precise recipient thanks to a unique address-port correspondence.
It differs from the router which routes instead at level 3 (internetworking) by interconnecting several local networks through the IP protocol and from the hub which is only a physical layer multi-port repeater, i.e. diffusive without addressing.
The wireless connection
 The term Wi-Fi refers to the technique and related devices that allow user terminals to connect to each other via a wireless local area network (WLAN).
The term Wi-Fi refers to the technique and related devices that allow user terminals to connect to each other via a wireless local area network (WLAN).
The Wi-Fi network is a telecommunications network, possibly interconnected with the Internet, conceptually comparable to a small-scale (local) cellular coverage network, through radio transceiver devices such as access points (APs) replacing traditional radio base stations of mobile radio networks (client-server architecture model).
There are various classes of wi-fi with different performances (as better specified in the details of the IEEE 802.11 standard), the main ones are:
- class b at 11 Mb/s
- class g at 54 Mb/s
- class n at 450 Mb/s
CONNECT TO THE INTERNET
Protocols

When we switch on our router (or connect to the operating system), it establishes an adsl connection to our ISP (operator) and it then redistributes it to the home network. There are various connection protocols:
PPPoE (“Point-to-Point Protocol over Ethernet”) indicates a network protocol that represents a new alternative for high-speed Internet connections used mainly for DSL services. PPPoE is a tunneling protocol that allows to encapsulate the IP level on a connection between two Ethernet ports while maintaining the characteristics of a PPP connection, for this reason it is used to “dial the number” virtually of another computer equipped with Ethernet connection and establish a point-to-point connection with it (hence the name of the protocol), on this connection IP packets are then transported according to the characteristics of the PPP.
PPPoA (“Point-to-Point Protocol over ATM – see above”, i.e. a “point-to-point protocol operating over Atm”) was previously widely used especially with USB modems. Now disused due to instability at high speeds.
The IP address and the MAC
 An IP address is a number that uniquely identifies a device connected to a network that uses Internet Protocol as its communication protocol. An IP address essentially performs two main functions: identifying a device on the network and providing its reachability path.
An IP address is a number that uniquely identifies a device connected to a network that uses Internet Protocol as its communication protocol. An IP address essentially performs two main functions: identifying a device on the network and providing its reachability path.
The IP address is a level 3 address of the ISO-OSI model which is necessary for indirect addressing through the homonymous IP network protocol or for interconnecting (internetworking) several different sub-networks within the TCP-IP paradigm of the Internet network. It contrasts with the level 2 physical address or MAC address used instead for direct addressing within a local subnet.
More precisely, the IP address is assigned to an interface (e.g. a network card) that identifies the network host, which can be a personal computer, a PDA, a router, household appliances in general, etc. It should be considered, in fact, that a host can contain more than one interface: for example, a router has several interfaces (minimum two) and for each one you need an IP address.
Public IP addresses and address ranges are issued and regulated by ICANN through a number of delegated organisations. Due to the saturation of the IPv4 space, ICANN has defined the new version of the IP protocol: IPv6 to overcome this inconvenience. This version is based on 128 bit addresses instead of 32 bits, which will allow the allocation of a much larger number of addresses.
File sharing (P2P)
 In IT and telecommunications, file sharing is the sharing of files within a common computer network. It can take place through a network with a client-server architecture (client-server) or peer-to-peer architecture.
In IT and telecommunications, file sharing is the sharing of files within a common computer network. It can take place through a network with a client-server architecture (client-server) or peer-to-peer architecture.
The most famous peer-to-peer networks are: Gnutella, OpenNap, Bittorrent, eDonkey, Kademlia.
These networks can search for a particular file by means of a URI Universal Resource Identifier, locate multiple copies of the same file in the network by means of cryptographic hashes, download from multiple sources at the same time, resume downloading the file after an interruption.
File-sharing programs are used directly or indirectly to transfer files from one computer to another on the Internet, or on Intranet corporate networks. This sharing has given rise to the peer-to-peer model.
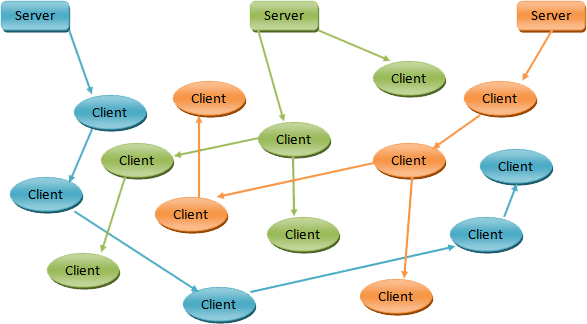
 Peer-to-peer (or P2P), i.e. equal network, means that it’s a computer network or any computer network that does not have hierarchical nodes in the form of fixed clients or servers (clients and servants), but a number of equivalent nodes (in English peer) that can act as both client and servant to the other nodes of the network.
Peer-to-peer (or P2P), i.e. equal network, means that it’s a computer network or any computer network that does not have hierarchical nodes in the form of fixed clients or servers (clients and servants), but a number of equivalent nodes (in English peer) that can act as both client and servant to the other nodes of the network.
This network model is therefore the antithesis of client-server architecture. Through this configuration any network node is able to start or complete a transaction. The equivalent nodes may differ in local configuration, processing speed, bandwidth and amount of stored data. The classic example of P2P is the file sharing network.
The Browser
IE – Edge – Chrome – Firefox – Opera
 The browser (/ˈbraʊzər/) or navigator is a program that allows you to take advantage of connectivity services on the Web and browse the World Wide Web, relying on the network protocols provided by the operating system (starting from application-level protocols such as HTTP, FTP, etc.) through appropriate APIs, allowing you to view the contents of the pages of websites and interact with them. The latter feature is supported by the browser’s ability to interpret HTML – the code with which most web pages are written – and to display it in hypertext form.
The browser (/ˈbraʊzər/) or navigator is a program that allows you to take advantage of connectivity services on the Web and browse the World Wide Web, relying on the network protocols provided by the operating system (starting from application-level protocols such as HTTP, FTP, etc.) through appropriate APIs, allowing you to view the contents of the pages of websites and interact with them. The latter feature is supported by the browser’s ability to interpret HTML – the code with which most web pages are written – and to display it in hypertext form.
Browsers are mainly used on personal computers, but also on other devices that allow surfing the Internet, such as PDAs and smartphones. The most well-known and popular ones are Internet Explorer, Mozilla Firefox, Google Chrome, Safari and Opera.
The first browser was developed by Tim Berners-Lee (one of the first pioneers of the WWW concept and founder of W3C), and was called WorldWideWeb. It was used for demonstration purposes, was only available for the NeXT operating system, and was later called Nexus.
The HTML language
 HyperText Markup Language (HTML) (literal translation: description language for hypertext) is the language usually used for hypertext documents available on the World Wide Web. In such documents, a stretch of text can be marked by inserting labels, tags, describing its function, colour, link, or other features. The content served by websites following a user request usually consists of an HTML document: a web browser downloads the HTML content and any linked documents from one or more web servers and processes them, i.e. interprets the code, in order to generate the desired page display on the computer screen.
HyperText Markup Language (HTML) (literal translation: description language for hypertext) is the language usually used for hypertext documents available on the World Wide Web. In such documents, a stretch of text can be marked by inserting labels, tags, describing its function, colour, link, or other features. The content served by websites following a user request usually consists of an HTML document: a web browser downloads the HTML content and any linked documents from one or more web servers and processes them, i.e. interprets the code, in order to generate the desired page display on the computer screen.
HTML is not a programming language (as it does not provide for any definition of variables, data structures, functions, control structures) but it’s only a markup language that describes the layout, formatting or graphic display (layout) of the content, textual or otherwise, of a web page through formatting tags. However, HTML supports the insertion of scripts and external objects such as images or movies. HTML (.html) or HTM (.htm) is also the common extension for recognising documents in this format.
HTML documents are usually stored on the hard disks of processing machines (computer servers) that are constantly connected to the Internet. A specific software called web server is installed on these machines, which is responsible for producing and sending documents to the browsers of users who request them using the HTTP protocol for data transfer.
Often the HTML document is generated completely or partially through an executable code resident on the Internet server able to interact with other applications on the server itself, such as a database, and then send the final result to the browser, creating the so-called dynamic pages with which a user can perform advanced interactive operations (for example, filtering articles within an on-line catalogue). This is the case for documents written in languages such as ASP, PHP or Perl.
The World Wide Web
 The World Wide Web (English name of origin), also known as the World Wide Web, is an Internet service that makes it possible to surf and enjoy a vast array of multimedia content and other services accessible to all or a selected number of Internet users.
The World Wide Web (English name of origin), also known as the World Wide Web, is an Internet service that makes it possible to surf and enjoy a vast array of multimedia content and other services accessible to all or a selected number of Internet users.
The main feature of the Web is that its contents are connected to each other (forming a hypertext, through so-called links, connections). And its services can be made available by Internet users themselves.
The birth of the Web dates back to 6 August 1991, the day Berners-Lee put the first website online on the Internet. Initially used only by the scientific community, CERN decided on 30 April 1993 to make the technology behind the Web public. This decision was followed by an immediate and wide-ranging success of the Web because of the possibility for anyone to become a publisher, its efficiency and, last but not least, its simplicity. With the success of the Web, the exponential and unstoppable growth of the Internet, which is still in progress today, and the so-called “Web Age”, began.
The Web is implemented through a set of standards, the main ones of which are as follows:
- HTML (and its derivatives): the markup language with which web pages are written and described;
- HTTP: the network protocol belonging to the application layer of the ISO/OSI model on which the Web is based;
- URL: the pattern of identification, and therefore of traceability, of the contents and services of the Web.
The peculiarity of Web contents is that they are not stored on a single computer but are distributed over several computers, a feature from which efficiency derives as they are not bound to a particular physical location. This peculiarity is achieved by the HTTP network protocol which allows to see the contents of the Web as a single set of contents even if they physically reside on a multitude of Internet computers scattered around the planet.
How a web page display works.
 Viewing a web page starts by typing the URL in the appropriate field of your web browser or clicking on a hyperlink in a previously viewed web page or other resource such as an e-mail. The web browser at that point behind the scenes starts a series of communication messages with the web server hosting that page in order to display it on the user terminal.
Viewing a web page starts by typing the URL in the appropriate field of your web browser or clicking on a hyperlink in a previously viewed web page or other resource such as an e-mail. The web browser at that point behind the scenes starts a series of communication messages with the web server hosting that page in order to display it on the user terminal.
First the server-name portion of the URL is resolved into an IP address using the global and distributed database known as the Domain Name System (DNS). This IP address is needed to send and receive packets from the web server.
The browser then requests the information by sending a request to that address. In the case of a typical web page, the HTML text of a page is requested first and immediately interpreted by the web browser, which then requests any images or files that will be used to form the final page.
Once the requested files have been received by the web server, the browser formats the page on the screen following the HTML, CSS, or other web language specifications. Each image and other resources are incorporated to produce the web page that the user will see.
VIRUS – ANTIVIRUS – FIREWALL
Viruses
 In computer science, a virus is software in the malware category which, once executed, is able to infect files in order to reproduce itself by making copies of itself, usually without being detected by the user. Viruses may or may not be directly harmful to the operating system that hosts them, but even in the best case they result in a certain waste of resources in terms of RAM, CPU and hard disk space. As a general rule, it is assumed that a virus can only directly damage the software of the machine that hosts it, although it can also indirectly cause damage to the hardware, for example by overclocking the CPU or stopping the cooling fan.
In computer science, a virus is software in the malware category which, once executed, is able to infect files in order to reproduce itself by making copies of itself, usually without being detected by the user. Viruses may or may not be directly harmful to the operating system that hosts them, but even in the best case they result in a certain waste of resources in terms of RAM, CPU and hard disk space. As a general rule, it is assumed that a virus can only directly damage the software of the machine that hosts it, although it can also indirectly cause damage to the hardware, for example by overclocking the CPU or stopping the cooling fan.
In common use, the term virus is frequently and improperly used as a synonym for malware, thus also indicating different categories of “pests”, such as worms, Trojans, dialers or spyware.
A virus consists of a set of instructions, just like any other computer program. It usually consists of a very small number of instructions, (from a few bytes to a few kilobytes), and is specialised to perform only a few simple operations and optimised to use as few resources as possible, so as to make itself as invisible as possible. The main characteristic of a virus is that it reproduces itself and then spreads in the computer every time the infected file is opened.
However, a virus in itself is not a self-executable program, just as a biological virus is not a life form in itself. In order to be activated, a virus must infect a host program, or a sequence of code that is launched automatically, such as a boot sector virus. The technique usually used by viruses is to infect executable files: the virus inserts a copy of itself into the executable file that it must infect, places a jump instruction at the first line of its copy and at the end of it places another jump at the beginning of the program’s execution. In this way, when a user launches an infected program, the virus is first imperceptibly executed, and then the program. The user sees the program running and does not realise that the virus is now running in memory and is performing the various operations contained in his code.
Mostly a virus makes copies of itself by spreading the epidemic, but it can also have other much more harmful tasks (deleting or ruining files, formatting the hard disk, opening backdoors, displaying messages, drawings or changing the appearance of the video, …).
Anti-viruses
 An antivirus is a software that detects and eliminates computer viruses or other harmful programs (malware) such as worms, Trojans and dialers.
An antivirus is a software that detects and eliminates computer viruses or other harmful programs (malware) such as worms, Trojans and dialers.
One of the main methods of function of an anti-virus software is based on the search in the RAM memory and/or inside the files present in a computer of a pattern typical of each virus (in practice each virus is composed of a precise number of instructions (code) that can be seen as a string of bytes, the program searches if this sequence is present inside the files or in memory). A pattern is also called “virus signature”. The success of this search technique is based on the constant updating of patterns that the antivirus is able to recognise, which is usually carried out by a group of people following reports from users and by groups specialising in the detection of new viruses.
 There is also another recognition technique called “heuristic search” which consists of analysing the behaviour of the various programs in search of suspicious instructions because they are typical of virus behaviour (such as searching for files or inserting routines within another file) or searching for small variants of viruses already known (by varying one or more instructions it is possible to obtain the same result with a slightly different program).
There is also another recognition technique called “heuristic search” which consists of analysing the behaviour of the various programs in search of suspicious instructions because they are typical of virus behaviour (such as searching for files or inserting routines within another file) or searching for small variants of viruses already known (by varying one or more instructions it is possible to obtain the same result with a slightly different program).
LIMITS OF AN ANTIVIRUS
It must be remembered that the antivirus is able to eliminate first of all only the viruses it recognizes, so all new viruses (new signifies both viruses that your antivirus does not recognise and those that have not yet been discovered) can go completely unnoticed and act without the antivirus intervening. Moreover, the antivirus can only intercept the virus when it has entered the computer and therefore has already infected a file or memory; at this point, depending on the virus, it can “disinfect” the file or memory by completely eliminating the virus or in some cases it is forced to “quarantine” the infected file and delete it due to the impossibility of recovering the original file.
You must continuously update your antivirus software to prevent malware that is already recognised (i.e. already entered in the software’s online database list) from being unrecognised and thus infecting your PC.
![]() VirusTotal is a free site that allows you to upload files up to 32 Mb for a TOTAL and complete Antivirus scan.
VirusTotal is a free site that allows you to upload files up to 32 Mb for a TOTAL and complete Antivirus scan.
Why Total?
Instead of scanning the file with a single antivirus engine, this site scans the file with each antivirus on the market, and displays a detailed report of the results obtained with each of the antivirus used*.
The strength lies in scanning the uploaded file not with just one antivirus (as we would all do with the one installed on our PC), but with about 50 different antivirus engines which, taken as a whole, manage to cope with each other’s shortcomings in terms of virus detection.
In short, if we have a file that we don’t know where it came from or our antivirus marks it as suspicious, let’s not be fooled and let’s get rid of any doubts with VirusTotal*!
*beware: to avoid leaks of sensitive data, we do not recommend uploading files containing personal information.
Firewalls
 A firewall is a passive perimeter defence component that can also perform functions of connection between two or more network sections.
A firewall is a passive perimeter defence component that can also perform functions of connection between two or more network sections.
Usually the network is divided into two sub-networks: one, called external, includes the entire Internet while the other internal, called LAN (Local Area Network), includes a more or less large section of a set of local computers.
A first closed definition of a firewall is the following: Hardware or software network apparatus that filters all incoming and outgoing packets, from and to a network or computer, applying rules that contribute to its security.
The computer communicates with the outside world via “ports”. The firewall opens or closes (and in any case monitors) all the ports to prevent unauthorised access.
See the PORT TEST section to verify the correct “closing” of all the computer ports.
CURIOSITY
HTML5 compatibility
Does your browser support the new HTML v5 standard? And how fast is it loading? Give it a rating!
Test your browser here for free!
Port Test
Not sure you have all the ports locked in your firewall?
Or do you want to try if the Remote Desktop port is open?
Test and map the secure ports and not on this page, directly here on Spaceclick!
Speedtest
Your line seems slow… do you want to know how fast you really navigate?
Test your line with Speedtest.net for free!

